Android Ethical Hacking
Learn how to make your Android application more secure.
Hi, in this article, I will describe some key points to have and avoid, so you can have a more secure Android application. Here I will describe only the general context and if you want to read more about each of them you can find easily more.
Having a secure application not only for Android apps but every software that you develop is a big deal, because, when we have data breaches or security flawless in our codes, this can bring problems for your company and your users, and no one wants to use something that is not secure.
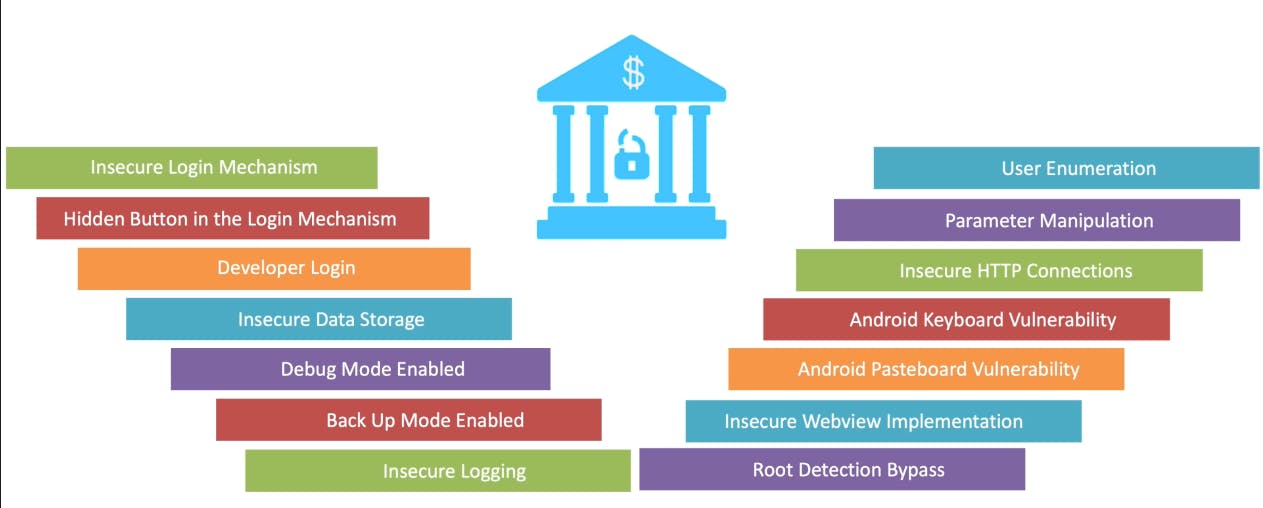
The image above point some insecure points of an Android application, that I will briefly describe below.
1 Exported flags.
Avoid using exported flag in your activities, hackers can have access to sensitive information.
When you export some activity in your manifest attackers can start them via activity manager, and if the activity is protected by a authentication for example you can start it without need to log in into the applicaiton.
You need to export only the activity that starts your application, but make sure that the rest of the declared activities are not exported. But if you need to export an activity, make sure that starting it from an ADB command for example does not impose security risks.
You can read more about it here.
2. Debuggable flag.
Never use debuggable true to release flavors. When you add debuggable flag for release flavor, anyone can see the logs of your application, and they can even try to debug the APK to understand better how your application works and find breaches.
And;
Using debbugable = true we can have access to a lot of features that are only used on debug flavor, like access the app database using adb run-as command and cat to fetch the database.
3. Use wisely the allowBackup flag.
It is easy to access the backup that the Android generates, on a device with root you can start the backup process and then extract the ab file, and have access to sharedPreferences, db, for example.
When allowing your application to use the Android backup system, you need to make sure that the files that you use are encrypted, database or shared preferences file.
Android now has better ways to configure the backup of your application, you can exclude and define which type of backup you want to enable for your application, but that does not exclude the fact that you can access the files.
You can read more about it here.
4. Production logs.
Avoid printing logs to the console on production build, anyone can have access to them, and if you log sensitive data you are putting the security of your users in danger.
5. Web views with JS enabled.
If the application is using a local html file we can replace the file and add some js code that executes with the user interation, even with remote webViews we can replace the URL and open another website.
You can read more about web view here.
6. Clipboard and keyboard dictionary.
Before Android 10 the clipboard and keyboard dictionary can be accessed through the terminal, someone can get your dictionary from the keyboard and get sensitive information.
You can see a project that demonstrate the problem here.
7. Detect rooted device.
If you are working with a banking application for example security is really important, and prevent users with root to access your application is important, because root give you access to a lot of things, some of them I described here. And there are some ways to detect a rooted device:
- Look for a package with name Superuser installed
- Look for Busy box (package that allows running sudo commands on Linux)
- Execute commands like SU and ID
- Run pm and look for superuser package.
8. Obfuscation techniques.
On android, the most popular technique is using ProGuard, that include some features like:
- Rename obfuscation
- String obfuscation
- Dummy code insertion
- And more.
You can read more about ProGuard here. It is essential to note that, if you plan to use ProGuard you need to properly configure it, otherwise it will bring you problems with crashes and unreadable crash reports.
You can also go to a step further and use DexGuard
9. Keys and secrets.
Avoid declaring your secrets on .xml files or .gradle files, add them o .properties files, declare them as environment variables or encrypt them on a file and add the decryption key on an environment variable.
You can read more here.
10. SSL connection.
Prefer to use HTTPS connection instead of HTTP always.
Android provide a way to declare when specific URL's needs to be accessed without HTTPS, if this is your case, and you can't use SSL
You can read more about here.
11. Certificate pinning.
Implement certificate pinning with your back end, to make sure that you are communicating with the right API and there is no one in the middle.
You can read more about here.
Some concepts from this article were taken from the course.
You also can read more about Android Security here.
